Sometimes we spend so much time protecting our websites that we forget about protecting our users. It is more efficient to be proactive than reactive.
For this reason its a good idea to set some security HTTP headers so that if your users do get targeted by a hacker that they won’t be able to as easily fool them into handing over their credentials.
Step 1:
First lets open up the LiteSpeed WebAdmin console by heading over to
https://yourwebsite.com:7080
Now click on the magnifying glass icon to edit the virtual host and navigate to context
Navigate to the context tab and hit add
Make the type “Static” and hit the skip icon to the upper-right to go next
Now fill out the following, in the URI section put “/” or any subdomain you want, set accessible radio button to yes and add the following in the Header Operations box
NOTE: It is a good idea to understand exactly what Content-Security-Policy does before adding it, as if you use this without checking first if your scripts are loading anything outside your domain name it will stop those scripts from loading in browsers.
Strict-Transport-Security: max-age=31536000; includeSubDomains
Content-Security-Policy: default-src https:
X-Content-Type-Options "nosniff" always
X-Frame-Options: SAMEORIGIN
Referrer-Policy: no-referrer-when-downgrade
Permissions-Policy: geolocation=(self ""),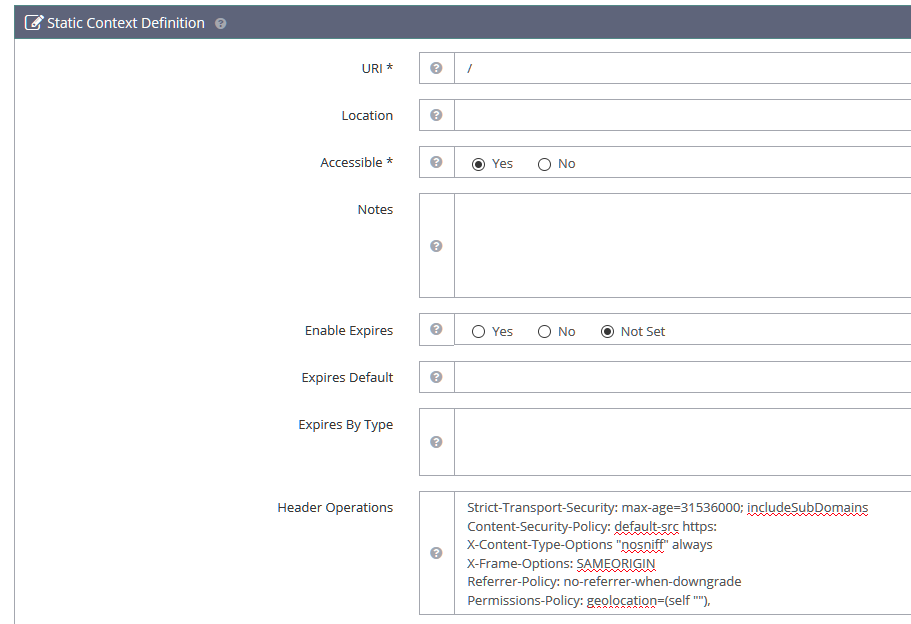
Now you can hit the save button in the upper right and reload OpenLiteSpeed
Step 2:
To check that your headers have been set correctly, you can visit https://securityheaders.com
And hopefully you’ll have a nice A+ result!
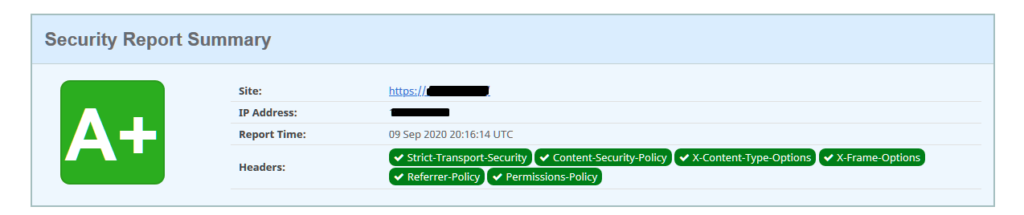
Notes:
If you would like to learn more about these headers I suggest researching them individually.
Especially if you would like to have a more fine-tuned setup.
Please note that some of these settings can break your website if it isn’t built to use HTTPS or if it has errors/bad-practices in its make-up, please research/test each individual header prior to going to production with them.
Admiring the commitment you put into your blog and
in depth information you provide. It’s great to come across a blog every once in a while that isn’t the same out of date rehashed material.
Fantastic read! I’ve bookmarked your site and I’m adding your RSS feeds to my Google account.
One problem – Strict-Transport-Security need only for HTTPS protocol, but if you put in Context – it will be for all domains, and will be intercepted.
If check HSTS here https://hstspreload.org/
Will be displayed:
Unnecessary HSTS header over HTTP
For this reason Strict-Transport-Security need use only on 443 virtual host.
This is true, but in my case I normally don’t use HTTP except as a redirect to HTTPS these days.
For X-Frame-Options more good be ‘deny’, like in OWASP Security Headers documentation.
Read this please: https://owasp.org/www-project-secure-headers/
This can break embedded content and is extreme. SAMEORIGIN will restrict it to content from the same origin (eg your domain name) and is the preferred option.
Content-Security-Policy: default-src https:
if i use this my website format disturbed and advertisement removed
You need to ensure that all local content is linked using relative URLs eg (/somedir/somecontent.jpg), not absolute(http://yoursite.com/somedir/somecontent.jpg).