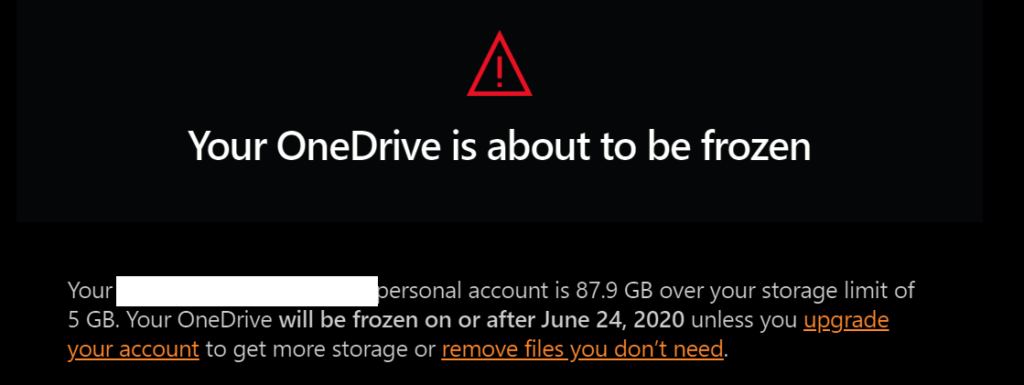
Recently I’ve been getting these emails from Microsoft saying that my OneDrive account is about to be frozen ( Apparently they decided to chop everyone’s storage down after the fact to 5GB and then charge people for the excess storage they’ve already used up thinking it was free /facepalm ).
Thing is that I’ve been so busy with Life especially with the Covid-19 pandemic going on that I really don’t care about sorting out my OneDrive right now.
That being said my home connection sucks, I mean it’s really bad.
On a good day I get about 5-6mbit/s down and at that rate it would take about 37 Hours to download my entire OneDrive storage to my local system, not to mention it would piss off everyone else who wants to use the internet in the house.
Then I thought why don’t I just transfer these files to my VPS since I have the excess storage anyways and my VPS’s connection is a much more palatable 100mbit/s+ down.
In comes obstacle one, OneDrive doesn’t officially support Linux, so we’ll be using rclone to connect and download our files instead.
Step 1:
First we need to install rclone
curl https://rclone.org/install.sh | sudo bash
Easy enough am I right?
Step 2:
We need to configure rclone to connect to our onedrive account so it can fetch and mount the files for us.
Thing is this process actually requires a web-browser for the authentication part, so you cannot do it easily via console. In my case I ended up installing VNC (for which you can check my tutorial below) and Firefox (via flatpak which I will post soon).
Run the configuration prompt and type new to create a new remote server configuration
root@oneserver:~# rclone config 2020/06/16 14:31:56 NOTICE: Config file "/root/.config/rclone/rclone.conf" not found - using defaults No remotes found - make a new one n) New remote s) Set configuration password q) Quit config n/s/q> n
Next you’ll be asked what type of storage you wish to configure, in my case OneDrive was 23rd down the list but this may change in the future so be sure to check
Type of storage to configure.
Enter a string value. Press Enter for the default ("").
Choose a number from below, or type in your own value
1 / 1Fichier
\ "fichier"
2 / Alias for an existing remote
\ "alias"
3 / Amazon Drive
\ "amazon cloud drive"
4 / Amazon S3 Compliant Storage Provider (AWS, Alibaba, Ceph, Digital Ocean, Dreamhost, IBM COS, Minio, etc)
\ "s3"
5 / Backblaze B2
\ "b2"
6 / Box
\ "box"
7 / Cache a remote
\ "cache"
8 / Citrix Sharefile
\ "sharefile"
9 / Dropbox
\ "dropbox"
10 / Encrypt/Decrypt a remote
\ "crypt"
11 / FTP Connection
\ "ftp"
12 / Google Cloud Storage (this is not Google Drive)
\ "google cloud storage"
13 / Google Drive
\ "drive"
14 / Google Photos
\ "google photos"
15 / Hubic
\ "hubic"
16 / In memory object storage system.
\ "memory"
17 / Jottacloud
\ "jottacloud"
18 / Koofr
\ "koofr"
19 / Local Disk
\ "local"
20 / Mail.ru Cloud
\ "mailru"
21 / Mega
\ "mega"
22 / Microsoft Azure Blob Storage
\ "azureblob"
23 / Microsoft OneDrive
\ "onedrive"
24 / OpenDrive
\ "opendrive"
25 / OpenStack Swift (Rackspace Cloud Files, Memset Memstore, OVH)
\ "swift"
26 / Pcloud
\ "pcloud"
27 / Put.io
\ "putio"
28 / QingCloud Object Storage
\ "qingstor"
29 / SSH/SFTP Connection
\ "sftp"
30 / Sugarsync
\ "sugarsync"
31 / Tardigrade Decentralized Cloud Storage
\ "tardigrade"
32 / Transparently chunk/split large files
\ "chunker"
33 / Union merges the contents of several upstream fs
\ "union"
34 / Webdav
\ "webdav"
35 / Yandex Disk
\ "yandex"
36 / http Connection
\ "http"
37 / premiumize.me
\ "premiumizeme"
38 / seafile
\ "seafile"
Storage> 23
Next you’ll be asked to enter Microsoft App Client Id and Secret, which we’ll ignore for now since we will be using the web authentication (just hit enter)
** See help for onedrive backend at: https://rclone.org/onedrive/ **
Microsoft App Client Id
Leave blank normally.
Enter a string value. Press Enter for the default ("").
client_id>
Microsoft App Client Secret
Leave blank normally.
Enter a string value. Press Enter for the default ("").
client_secret>
Next it will ask you if you wish to enter advanced configuration, hit no unless you have something special planned
Edit advanced config? (y/n) y) Yes n) No (default) y/n> n
Now is when you’ll be asked if you would like to auto-configure, and for this step we type yes
Use auto config? * Say Y if not sure * Say N if you are working on a remote or headless machine y) Yes (default) n) No y/n> y
Now is when either your browser will open up for you or you’ll have to manually go to the link (note that I wasn’t able to connect to this port remotely, so it may be that you have to open it locally), once you go there you’ll be asked to login to your Microsoft account and allow rclone a bunch of privileges it needs to do its thing
If your browser doesn't open automatically go to the following link: http://127.0.0.1:53682/auth?state=SECRETHERE Log in and authorize rclone for access Waiting for code... Got code
Next we’ll be asked to describe exactly what type of account this is, which is a little redundant to be honest.. but well.. select 1 for OneDrive
Choose a number from below, or type in an existing value 1 / OneDrive Personal or Business \ "onedrive" 2 / Root Sharepoint site \ "sharepoint" 3 / Type in driveID \ "driveid" 4 / Type in SiteID \ "siteid" 5 / Search a Sharepoint site \ "search" Your choice> Your choice> 1
Next it will search for “drives” on the remote server, if you happen to have multiple drives you can pick which one. In my case I only have one so I select 0
Found 1 drives, please select the one you want to use: 0: (personal) id=uniqueid834avsaf Chose drive to use:> 0
Now it will ask you to confirm the root of the drive, just type yes
Found drive 'root' of type 'personal', URL: https://onedrive.live.com/?cid=uniqueid834avsaf Is that okay? y) Yes (default) n) No y/n> y
At this point it will ask you to confirm that the access token was set correctly, type yes again
[onedrive]
type = onedrive
token = {"access_token":"AWHOLEBUNCHOFSESSIONTOKENTEXTTHATYOUSHOULDNTSHAREWITHANYONE","expiry":"2020-06-16T15:40:51.775771327Z"}
drive_id = uniqueid834avsaf
drive_type = personal
--------------------
y) Yes this is OK (default)
e) Edit this remote
d) Delete this remote
y/e/d> y
Now that were done with the configuration we can type quit
Current remotes: Name Type ==== ==== onedrive onedrive e) Edit existing remote n) New remote d) Delete remote r) Rename remote c) Copy remote s) Set configuration password q) Quit config e/n/d/r/c/s/q> q
Step 3:
Now lets create the folder we will mount this OneDrive to
mkdir ~/OneDrive
We need to decide what type of mounting we want, in this case we wish to have full read/write access to our files even if they disappear from the server so we use –vfs-cache-mode full
But there are many modes so be sure to check the documentation in case you don’t need a full copy (https://rclone.org/commands/rclone_mount/#file-caching)
rclone --vfs-cache-mode full mount onedrive: ~/OneDrive
And we’re done!
Now we can try to copy the files over to a local directory using a second SSH shell
mkdir ~/OneDriveBackup cd ~/OneDrive rsync -avzh --ignore-errors * ~/OneDriveBackup/2 Comments